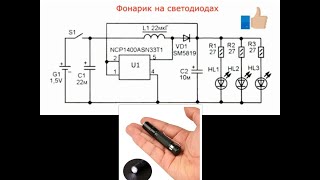
This video explains what a Pass the Hash attack is and demonstrates how an attacker can leverage the LanMan or NTLM hash of a user’s password to authenticate to a directory or resource without ever obtaining the user’s plaintext password.
To learn more about this attack and how to mitigate, detect and respond to it, go to: [ Ссылка ]
Learn about other attacks in our attack catalog: [ Ссылка ]